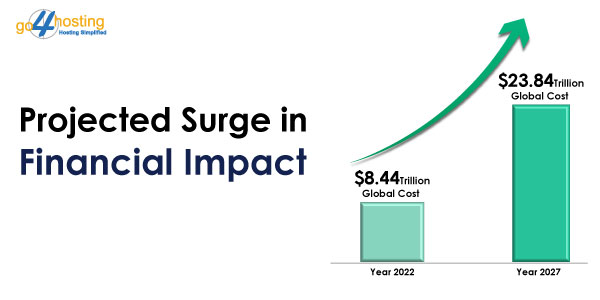
Did you know that in March 2022, the Lapsus$ hacking group stole 37GB of data from Microsoft’s Azure DevOps server? This data breach also exposed the source code of multiple projects. It’s not the first incident of an attack on cloud servers. In the past few years, numerous companies have become targets of attackers; in the future, we may see a rise in the number. To protect against these vulnerabilities, companies must adopt strategies to secure their cheap cloud servers assets.
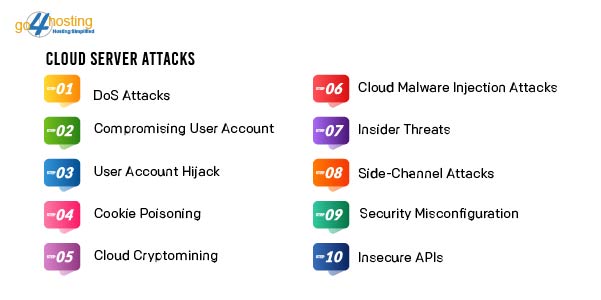
Cloud Server Attacks: Types
An attack on cheap cloud hosting in India may be executed in multiple ways. However, the aim of each invasion is the same: to exploit the vulnerabilities in the storage, access, and management of cloud-based data. Consequently, it can result in data loss, financial harm, and damage to an organization’s reputation. Before delving into the strategies to safeguard cloud servers against these attacks, let’s first understand their types.
- DoS Attacks
Denial-of-Service (DoS) renders a computer or network resource inaccessible to its intended users. It floods cheap cloud servers with excessive traffic, overwhelming the system and rendering it incapable of processing legitimate requests. Its consequences are severe, leading to disruptions in critical services, financial losses, and harm to an organization’s reputation.
- Compromising User Account
The compromise of a user account usually occurs when an attacker accesses the account by manipulating the owner. They execute the same either by deceiving the user into disclosing their login credentials or exploiting a system or application vulnerability used by the user.
- User Account Hijack
During user account hijacks, attackers gain unauthorized access or control of cheap cloud hosting in India. For instance, attackers may employ password-cracking methods to gain entry to a cloud account. They then use the associated resources for personal gain or to steal and manipulate the data stored in the cloud.
- Cookie Poisoning
Cookies retain information about a user’s preferences and browsing history. It is commonly used to personalize the user experience or monitor their activity. In SaaS and various cloud applications, cookies frequently hold credential data. It makes them susceptible to manipulation by attackers seeking unauthorized access to these applications.
Cookie poisoning involves the unauthorized modification or introduction of malicious content into a cookie.
- Cloud Cryptomining
During a cloud cryptomining, attackers employ stolen or compromised credentials to gain unauthorized access to cheap cloud servers resources, such as virtual machines or containers. Their objective is to exploit these resources for cryptomining purposes. Additionally, they may resort to malware or other unauthorized methods to access cloud resources.
- Cloud Malware Injection Attacks
In cloud malware injection attacks, malevolent software, such as viruses or ransomware, is introduced into cloud computing resources or infrastructure. It enables the attacker to compromise the targeted resources. Thus potentially leading to the theft or destruction of data or the unauthorized utilization of the resources for their own objectives.
- Insider Threats
In a cheap cloud server environment, insider threats involve individuals within an organization engaging in unauthorized access or misuse of resources. Additionally, there is the possibility of accidental exposure of assets to risks through their actions. Detecting and preventing insider threats can pose significant challenges because the individuals involved often have legitimate access to cloud assets.
- Side-Channel Attacks
In cloud hosting in India, attackers can execute side-channel attacks by deploying a malicious virtual machine on a legitimate physical host used by the cloud customer. It provides attacker access to confidential information on the targeted machine. It can extract sensitive data, such as passwords or encryption keys, and can potentially disrupt a system’s operation or manipulate its behavior.
- Security Misconfiguration
Security misconfiguration occurs when cloud computing resources and infrastructure are not adequately configured to safeguard against cyber threats. It may involve:
- Neglecting to establish appropriate access controls.
- Inadequately configuring and securing systems and applications.
- Overlooking regular updates and patches for systems and applications.
- Insecure APIs
APIs lacking robust security measures may harbor vulnerabilities that hackers can exploit to infiltrate systems or access data. These vulnerabilities encompass inadequately documented shadow APIs and API parameters susceptible to injection attacks.
Cloud Server Attacks: Preventive Measures
Now that we have a clear understanding of cheap cloud servers attacks let’s look at the best practices that can help to prevent and mitigate the same:
- Data Encryption
Securing data through encryption is crucial in cheap cloud hosting in India. Encryption transforms data into an unreadable format unless the appropriate decryption key is employed. Thus, even if an unauthorized party gains access to the data, they cannot decipher or comprehend it. It safeguards sensitive and confidential information against unauthorized access.
Encryption is applied at various stages:
- At-rest encryption
It encrypts data stored on a hard drive or within a cloud storage service. The purpose is to shield data during inactivity, preventing unauthorized parties from reading or accessing it.
- In-transit encryption
It pertains to encrypting data during transmission across networks, such as when it is sent to or received from a cheap cloud server provider. It safeguards data while in transit, preventing interception and unauthorized reading.
- In-use encryption
It involves encrypting data during usage or processing. Homomorphic encryption is a technique that enables processing data in its encrypted form. Through this method, computations are performed on the ciphertext, ensuring continual protection of the data.
- Enforcing Secure API Access
Ensuring that your clients are exclusively connected with cloud applications through secure APIs is important for several reasons:
- Security
APIs are the primary entry point for clients to interact with cloud applications and data. Securing them against cheap cloud servers attacks is critical to thwart unauthorized access to sensitive data and resources.
- Authentication and Authorization
Secure APIs can implement diverse mechanisms like token-based authentication, multi-factor authentication, and role-based access controls. These measures ensure that only authorized clients possess the privilege to access the cloud application and its
associated resources.
- Data Validation
Using secure APIs empowers organizations to validate the data received from clients before processing it. This validation process ensures the data adheres to the correct format and lacks malicious payloads.
- Managing Access to Cloud Services
Controlling access to cheap cloud hosting in India is crucial for minimizing the potential risk of cyber attacks. Organizations can enhance their security by limiting the number of individuals accessing resources and data.
Several instances illustrate how access restrictions can effectively prevent cloud-based attacks:
- Limiting access to cloud storage resources is a preventive measure against unauthorized individuals attempting to access and extract sensitive data.
- Restricting access to applications hosted in the cloud is a prudent step to stop unauthorized individuals from initiating DoS attacks. Thus safeguarding these applications from becoming unavailable to legitimate users.
- Controlling access to cheap cloud hosting in India helps prevent unauthorized users from compromising virtual machines. Thereby averting potential data breaches.
- Regulating access to cloud services is vital in preventing privileged insiders from abusing their access privileges. Thereby minimizing the risk of data theft or damage.
- Utilize CSPM tool
A cloud security posture management (CSPM) solution is a valuable tool for organizations to oversee and safeguard their cheap cloud servers. It plays a crucial role in defending against cloud-based threats through the following mechanisms:
- Asset Management
The CSPM solution facilitates identifying and cataloging an organization’s cloud assets, encompassing systems, applications, stored data, and user groups with cloud access. This comprehensive view aids in enhancing understanding of the cheap cloud servers environment. Moreover, it helps pinpoint potential vulnerabilities susceptible to exploitation by malicious entities.
- Compliance Oversight
A CSPM solution enables organizations to identify and address any compliance-related issues. This proactive approach helps mitigate non-compliance risks, safeguarding the organization from potential vulnerabilities.
- Threat Detection
Through continuous monitoring of cloud assets for unusual activities or potential vulnerabilities, the CSPM plays a vital role in early threat identification. This timely detection empowers organizations to take prompt corrective actions. Thus mitigating threats before they escalate and cause harm.
Leveraging a CSPM tool is imperative for organizations seeking to enhance the security of their cheap cloud hosting in India. It effectively manages assets, ensures compliance, and proactively detects and addresses potential threats.
Wrapping Up

As we navigate this digital transformation era, where the reliance on cloud computing is paramount, cheap cloud servers attack preventive measures have become necessities. They form the cornerstone of a resilient defense strategy, helping organizations withstand the evolving threat landscape.
In light of these challenges,go4hosting stands ready to assist you in fortifying your cloud security posture. Safeguard your cloud infrastructure, protect your data, and ensure business continuity with our tailored offerings.